FrameFlow's Rogue Machine Event Monitor searches your network for unrecognized systems and alerts you if any are detected. Use it to receive an immediate warning if a connection occurs without permission. This tutorial will teach you how to set up a Rogue Machine Event Monitor for exactly this purpose.
To begin, choose whether or not you want the event monitor to search for rogues in the local NetBIOS network. By default, the monitoring service runs in the LocalSystem account. To use this option, set the service to run in a domain account instead.
After that, enter the IP address range you want to check for rogues. Follow the format exemplified below when entering IP ranges.
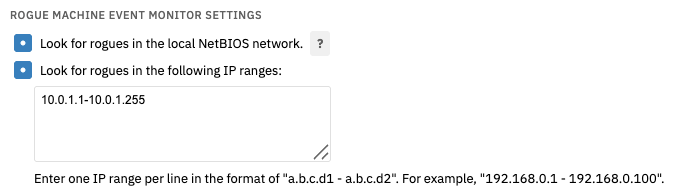 Scan Settings
Scan Settings
The next four options let you choose the methods of rogue detection you want to employ. You can use any combination of ping, ARP, HTTP, and SNMP requests. Click the question mark icons on the right-hand side of these options to access tips on using each request type.
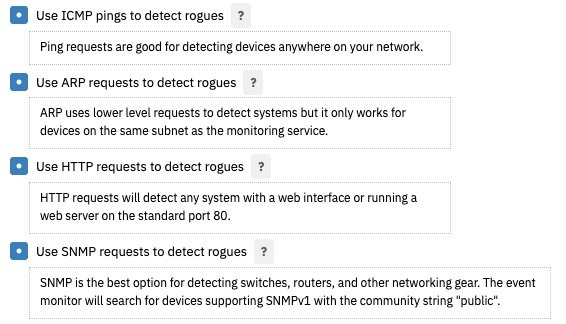 Request Type Options
Request Type Options
Next, choose the level of alert you want to receive if the list of detected rogues changes.
 Detected Rogues List Change Alert Option
Detected Rogues List Change Alert Option
The final option lets you specify rogue machines that, if detected, the event monitor will ignore. Enter a comma-separated list of the names or IP addresses of the systems you want to ignore. To find the names of detected machines, run the event monitor once and check the event text for the names of rogues in your environment.
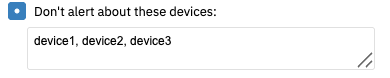 Ignore Rogues Option
Ignore Rogues Option
This tutorial taught you how to begin monitoring your IT environment for rogue machines with the Rogue Machine Event Monitor. For more documentation on this event monitor, visit its Technical Resources guide. Keep an eye out for new tutorials on FrameFlow's robust features and functionality coming soon!
More IT Monitoring Features